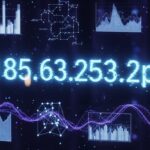
It often starts quietly. A founder checking analytics late at night notices an unfamiliar entry in the server logs. An entrepreneur reviewing security reports pauses at a strange-looking identifier: 185.63.253.2pp. It doesn’t immediately explain itself, yet it feels important. In today’s digital ecosystem, these small technical details often tell larger stories about connectivity, security, and how modern systems communicate behind the scenes.
This article explores 185.63.253.2pp not as a random string, but as a representative example of how identifiers, IP-like formats, and extensions shape the invisible infrastructure of the internet. For tech readers, founders, and entrepreneurs, understanding such elements is no longer optional. It is part of digital literacy in an increasingly connected world.
What 185.63.253.2pp Represents in a Connected Environment
At first glance, 185.63.253.2pp resembles an IP address, a familiar concept for anyone who has worked with websites, cloud platforms, or networked applications. Traditional IP addresses act like digital street addresses, guiding data to the correct destination. When a suffix like “pp” appears, it introduces ambiguity and curiosity.
In real-world practice, identifiers similar to 185.63.253.2pp often emerge in logs, custom routing systems, experimental configurations, or proprietary tagging methods used by platforms to add contextual meaning. For entrepreneurs building digital products, this highlights an important truth: not everything in your technical stack will look textbook-perfect. Systems evolve, adapt, and sometimes extend conventions for specific needs. Understanding this prevents panic and encourages informed investigation rather than guesswork.
Why Identifiers Like 185.63.253.2pp Matter to Founders
For founders and business leaders, technical identifiers are not just for engineers. They influence performance, trust, and scalability. Seeing 185.63.253.2pp in monitoring tools or backend systems can signal anything from a custom proxy route to a tagged request source.
The real value lies in interpretation. Instead of ignoring unfamiliar identifiers, successful teams ask structured questions. Where did it originate? Is it internal or external? Does it correlate with traffic spikes or system behavior changes? In modern startups, where data-driven decisions guide growth, these details often reveal optimization opportunities or early warnings.
The Role of Custom Identifiers in Modern Infrastructure
Modern digital infrastructure rarely relies on plain, unmodified standards. Cloud providers, CDNs, analytics tools, and security layers frequently extend identifiers to encode additional information. 185.63.253.2pp can be understood as part of this broader trend where context matters as much as the core address.
For example, adding suffixes or markers allows systems to differentiate between regions, protocols, or internal processing paths without redesigning entire architectures. Entrepreneurs building scalable platforms benefit from recognizing how these patterns work, because they mirror the same logic used in advanced systems.
Real-World Scenarios Where 185.63.253.2pp Appears
Identifiers like 185.63.253.2pp most commonly appear in backend environments rather than customer-facing interfaces. You might encounter them while reviewing access logs, firewall reports, or API gateway analytics. In these contexts, they function as breadcrumbs, helping teams trace activity across complex systems.
For tech-focused founders, this is particularly relevant during growth phases. As traffic increases and systems become more distributed, clarity about where requests come from and how they move through your stack becomes critical. An unfamiliar identifier is not necessarily a threat, but it is always a signal worth understanding.
Interpreting 185.63.253.2pp Through a Security Lens
Security is often the first concern when something unfamiliar appears. While 185.63.253.2pp may look suspicious at first, responsible analysis avoids assumptions. Many security incidents stem not from unknown identifiers themselves, but from how teams respond to them.
A structured approach involves checking whether the identifier aligns with known services, internal tools, or third-party integrations. Entrepreneurs who cultivate this mindset reduce false alarms while still maintaining vigilance. This balance is essential in an era where overreaction can be as costly as negligence.
Understanding the context behind identifiers strengthens both security posture and decision-making confidence.
Table: Common Contexts Where 185.63.253.2pp–Style Identifiers Are Found
| Context Area | Typical Purpose | Business Relevance |
|---|---|---|
| Server Logs | Tracking request sources and behavior | Performance tuning and debugging |
| Security Monitoring | Identifying access patterns | Risk assessment and threat detection |
| Analytics Systems | Tagging traffic or experimental routing | Data accuracy and growth insights |
| Cloud Infrastructure | Internal routing or proxy identification | Scalability and reliability planning |
| Development Environments | Testing custom configurations | Faster iteration and reduced deployment risk |
This table illustrates that identifiers like 185.63.253.2pp are not anomalies but practical tools embedded in modern workflows.
Why Entrepreneurs Should Care Beyond the Technical Team
One of the biggest misconceptions in startups is that infrastructure details belong solely to engineers. In reality, understanding identifiers such as 185.63.253.2pp empowers founders to ask better questions and make informed trade-offs.
When leaders grasp how systems communicate, they can align technical decisions with business goals more effectively. Whether evaluating a new hosting provider, discussing security budgets, or prioritizing platform stability, this knowledge turns abstract discussions into strategic conversations.
Avoiding Misinterpretation and Over-Optimization
There is a temptation, especially among data-driven founders, to over-analyze every unfamiliar detail. While 185.63.253.2pp deserves attention, it does not always demand action. The key lies in proportional response.
Understanding when an identifier is informational versus actionable saves time and resources. Mature organizations develop playbooks for such scenarios, ensuring consistency and clarity. Entrepreneurs who adopt this mindset early create calmer, more resilient teams.
The Broader Lesson Behind 185.63.253.2pp
Beyond its technical nature, 185.63.253.2pp symbolizes a broader truth about digital business. Success today depends on fluency in systems that customers never see. The invisible layers of infrastructure quietly shape user experience, trust, and growth.
By paying attention to these layers, founders position themselves to anticipate issues rather than react to crises. This proactive understanding often distinguishes sustainable companies from those that struggle under complexity.
Conclusion
What begins as a puzzling string like 185.63.253.2pp can become a catalyst for deeper understanding. For entrepreneurs, tech readers, and founders, the value lies not in memorizing technical formats, but in developing the habit of informed curiosity.
In a world where digital systems underpin almost every business model, fluency in these subtle signals is a form of leadership. When you recognize what identifiers represent, ask the right questions, and respond with context, you move from reactive management to confident stewardship of your digital ecosystem.